Wannacry, the hybrid malware that brought the world to its knees
Security Affairs
OCTOBER 31, 2022
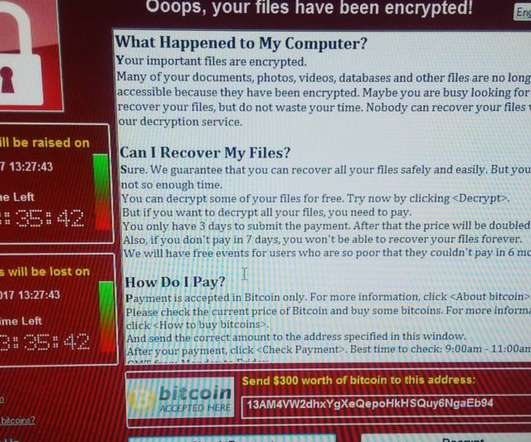
Reflecting on the Wannacry ransomware attack, which is the lesson learnt e why most organizations are still ignoring it. The cryptolocker had the task of encrypting the data of the affected system; The exploit was to infect the victim’s local network, if not properly updated, through the SMB protocol vulnerability.













Let's personalize your content