Group Health Cooperative data breach impacted 530,000 individuals
Security Affairs
APRIL 10, 2024
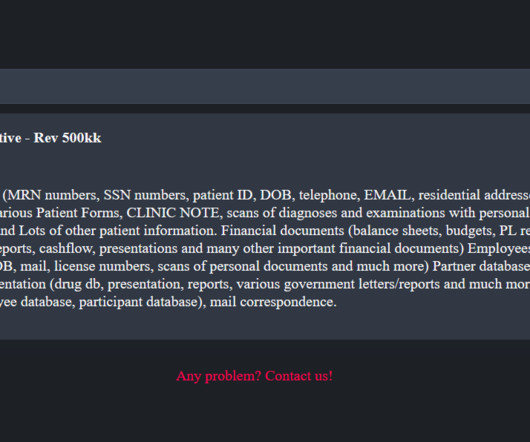
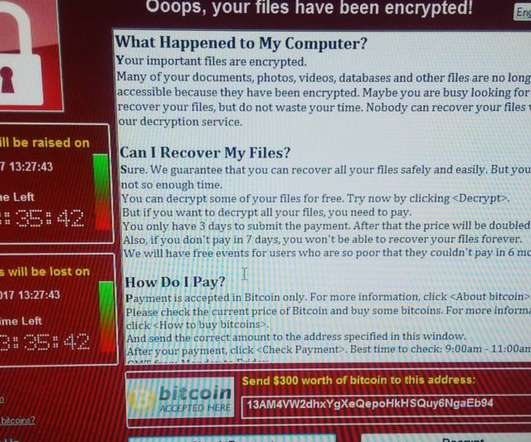
“The attacker attempted to encrypt GHC-SCW’s system but was unsuccessful.” ” The potentially compromised PHI may have included member/patient name, address, telephone number, e-mail address, date of birth and/or death, social security number, member number, and Medicare and/or Medicaid number. .”
































Let's personalize your content