Google: China dominates government exploitation of zero-day vulnerabilities in 2023
Security Affairs
MARCH 28, 2024
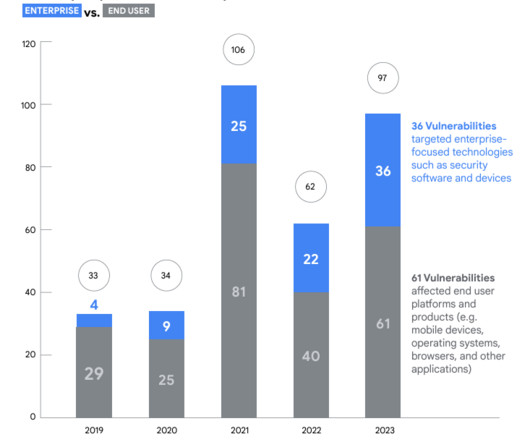
Google’s Threat Analysis Group (TAG) and Mandiant reported a surge in the number of actively exploited zero-day vulnerabilities in 2023. In 2023, Google (TAG) and Mandiant discovered 29 out of 97 vulnerabilities exploited in the wild. ” reads the report published by Google TAG. ” continues the report.













Let's personalize your content