Ransomware at IT Services Provider Synoptek
Krebs on Security
DECEMBER 27, 2019
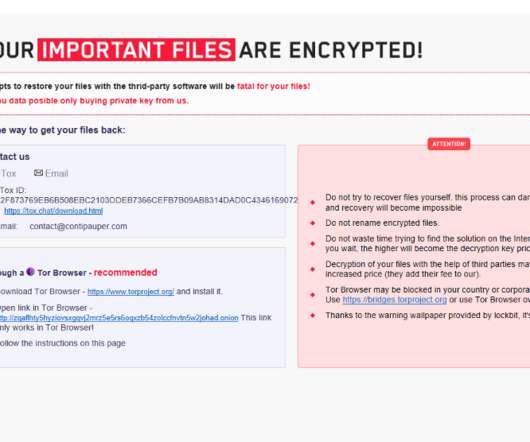
Synoptek , a California business that provides cloud hosting and IT management services to more than a thousand customer nationwide, suffered a ransomware attack this week that has disrupted operations for many of its clients, according to sources. A now-deleted Tweet from Synoptek on Dec.













Let's personalize your content