Navigating the Digital Landscape: Insights from the 2024 Thales Digital Trust Index
Thales Cloud Protection & Licensing
FEBRUARY 7, 2024
Additionally, the frustration with intrusive advertising (71%), cumbersome password resets (64%), and repetitive data entry (64%) indicate a growing demand for smoother digital experiences. The Rising Demand for Transparent and Ethical AI Use Consumer skepticism towards AI in digital interactions is increasingly evident.

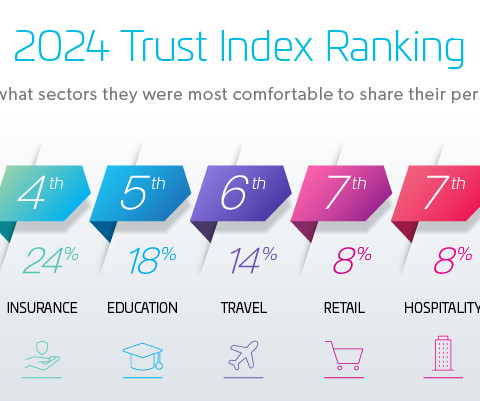




























Let's personalize your content