The Scammers’ Playbook: How Cybercriminals Get Ahold of Your Data
eSecurity Planet
SEPTEMBER 14, 2022
A major focus of cybersecurity as an industry is its efforts to detect, root out, and respond to potential fraudsters attempting to trick companies and people out of their money, data, or both. According to data from the Federal Reserve , the 55-69 age group currently controls 41.2% So why do scammers go after older individuals more?











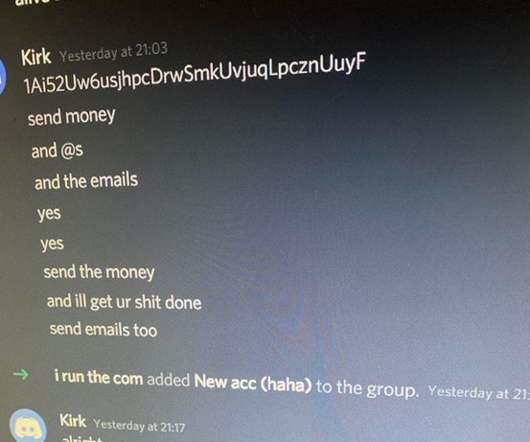
















Let's personalize your content