SolarWinds Attack: Microsoft sheds lights into Solorigate second-stage activation
Security Affairs
JANUARY 21, 2021
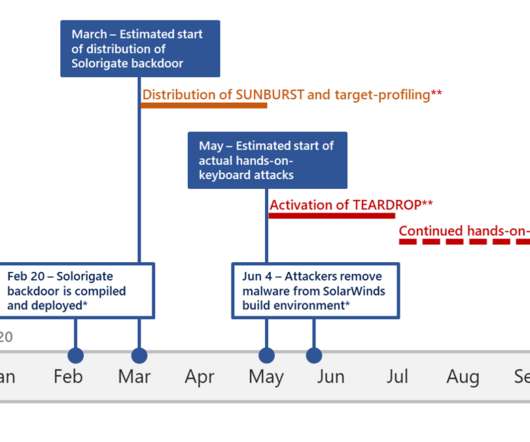
Microsoft experts analyzed forensic data across the entire environment of impacted organizations to discover how the attackers made lateral movements and how long they remaining within their target networks. The experts conducted a deep analysis of data collected by Microsoft 365 Defender data and Microsoft Defender telemetry.











Let's personalize your content