New Android malicious library Goldoson found in 60 apps +100M downloads
Security Affairs
APRIL 15, 2023
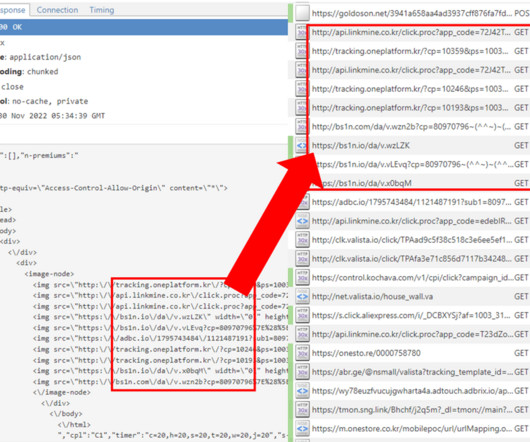
The Goldoson library was discovered by researchers from McAfee’s Mobile Research Team, it collects lists of applications installed on a device, and a history of Wi-Fi and Bluetooth devices information, including nearby GPS locations. It is important to highlight that the library was not developed by the authors of the apps.













Let's personalize your content