AI & ML Cybersecurity: The Latest Battleground for Attackers & Defenders
eSecurity Planet
FEBRUARY 11, 2022
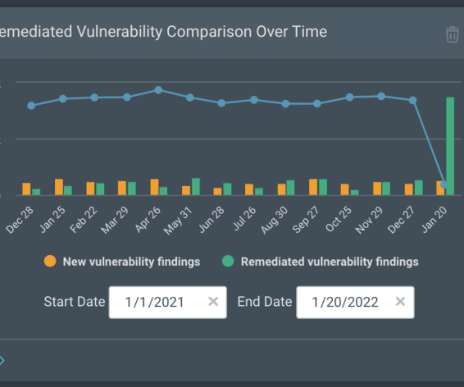
Even better, security tools like behavioral analytics can spot attacks simply by noticing anomalous activity, important technology for catching zero-day threats and adversarial attacks. Machine learning systems help make decisions based on collected data and self-adjust their model when detecting new patterns.















Let's personalize your content