Calendar Meeting Links Used to Spread Mac Malware
Krebs on Security
FEBRUARY 28, 2024
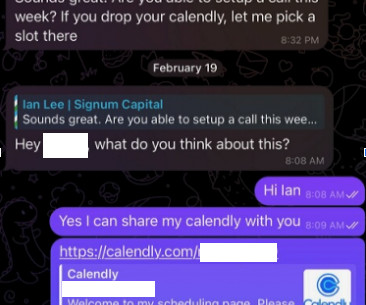
The attackers impersonate established cryptocurrency investors and ask to schedule a video conference call. The investor expressed interest in financially supporting Doug’s startup, and asked if Doug could find time for a video call to discuss investment prospects. “We are actively working on fixing these problems.





















Let's personalize your content