Hackers target Docker servers to deploy the new Kinsing cryptocurrency miner
Security Affairs
APRIL 6, 2020
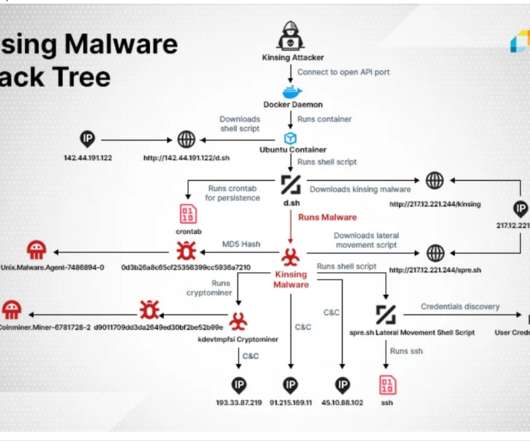
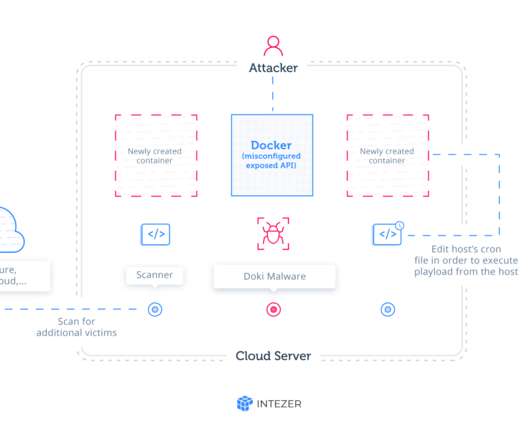
Experts uncovered a hacking campaign that is breaching Docker clusters to deploy a new crypto-mining malware tracked as Kinsing. ” The Kinsing malware abuses the resources of the Docker installations to mine cryptocurrency, hackers exploit unprotected open Docker API port to instantiate an Ubuntu container. “The spre.
















Let's personalize your content