No, I Did Not Hack Your MS Exchange Server
Krebs on Security
MARCH 28, 2021
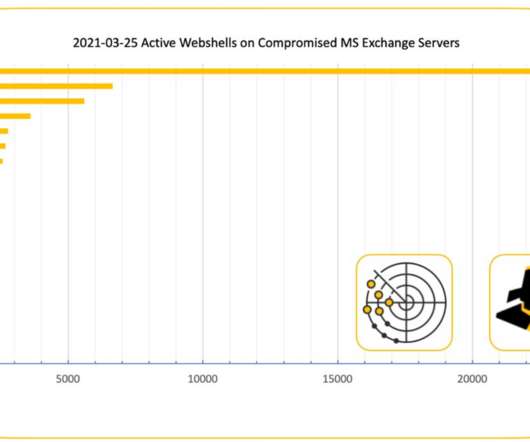
The Shadowserver Foundation , a nonprofit that helps network owners identify and fix security threats , says it has found 21,248 different Exchange servers which appear to be compromised by a backdoor and communicating with brian[.]krebsonsecurity[.]top krebsonsecurity[.]top top (NOT a safe domain, hence the hobbling). At Least 30,000 U.S.
















Let's personalize your content