No, I Did Not Hack Your MS Exchange Server
Krebs on Security
MARCH 28, 2021
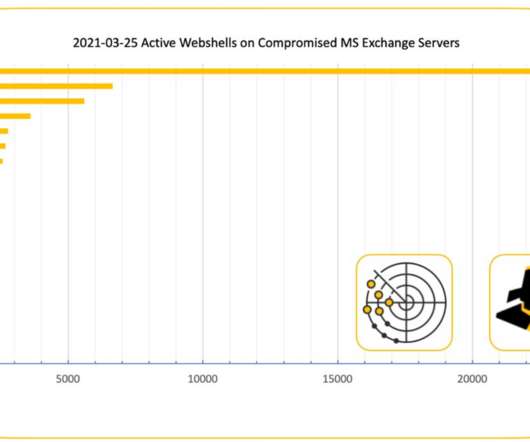
The group looks for attacks on Exchange systems using a combination of active Internet scans and “honeypots” — systems left vulnerable to attack so that defenders can study what attackers are doing to the devices and how. Here are a few of the more notable examples , although all of those events are almost a decade old.



























Let's personalize your content