Supply-Chain Attack against the Electron Development Platform
Schneier on Security
AUGUST 8, 2019
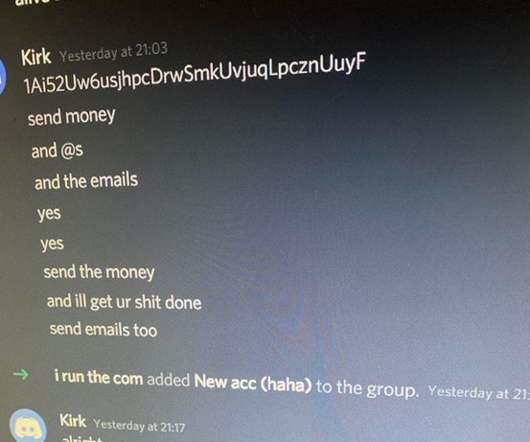
Electron is a cross-platform development system for many popular communications apps, including Skype, Slack, and WhatsApp. Basically, the Electron ASAR files aren't signed or encrypted, so modifying them is easy. Security vulnerabilities in the update system allows someone to silently inject malicious code into applications.
















Let's personalize your content