At Least 30,000 U.S. Organizations Newly Hacked Via Holes in Microsoft’s Email Software
Krebs on Security
MARCH 5, 2021
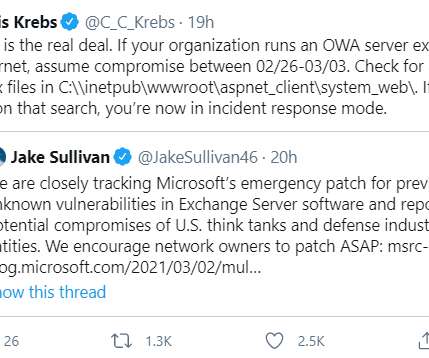
The espionage group is exploiting four newly-discovered flaws in Microsoft Exchange Server email software, and has seeded hundreds of thousands of victim organizations worldwide with tools that give the attackers total, remote control over affected systems. The backdoor web shell is verifiably present on the networks of thousands of U.S.


















Let's personalize your content