Tricky Phish Angles for Persistence, Not Passwords
Krebs on Security
JANUARY 7, 2020
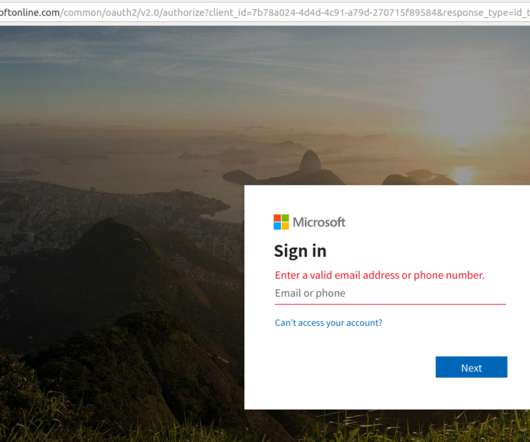
Also, the resulting compromise is quite persistent and sidesteps two-factor authentication, and thus it seems likely we will see this approach exploited more frequently in the future. “Even employees who are trained on security are trained to make sure it’s a legitimate site before entering their credentials.





















Let's personalize your content