Welcome to the era of the industrial cloud
OpenText Information Management
DECEMBER 10, 2019
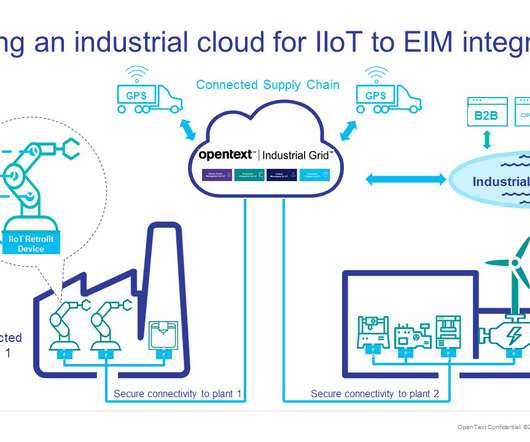
The industrial Internet of Things (IIoT) is having a profound effect on how manufacturing organizations share information.
OpenText Information Management
DECEMBER 10, 2019
The industrial Internet of Things (IIoT) is having a profound effect on how manufacturing organizations share information.

IT Governance
MAY 7, 2024
Source (New) IT services USA Yes 1,382 Worthen Industries Source 1 ; source 2 (Update) Manufacturing USA Yes 1,277 R.J. Source (New) Manufacturing USA Yes Unknown Human Events. Most notably, it’s banning bad default passwords on IoT (Internet of Things) devices, becoming the first country to do so.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

eSecurity Planet
NOVEMBER 19, 2021
IoT security is where endpoint detection and response ( EDR ) and enterprise mobility management ( EMM ) meet the challenges of a rapidly expanding edge computing infrastructure. As the enterprise attack surface grows, IoT is yet another attack vector organizations aren’t fully prepared to defend.

CGI
FEBRUARY 18, 2016
What does the resurgence of vinyl records say about IoT? It also led me to think about vinyl in the context of an IoT ecosystem and the user experience. For those of you interested in finding out more about IoT ecosystems, my colleague Gemma Beard has written a couple of excellent blogs [link] and [link] ). p.butler@cgi.com.

IBM Big Data Hub
JULY 28, 2023
It is the manufacturers’ job to make sure you’re sitting comfortably in your chair, your car is operating safely, and your gas is flowing when you need it. Manufacturers are the unsung heroes who make sure we’re safe, day in and day out. They do not get famous if they do their job well.

eSecurity Planet
FEBRUARY 16, 2021
Most device or software manufacturers place backdoors in their products intentionally and for a good reason. Always change the default passwords for any IoT devices you install before extended use. However, a growing number of botnet attacks are used against IoT devices and their connected networks. Backdoors. with no internet.

eDiscovery Daily
MARCH 29, 2018
National Archives and Records Administration, and as trial lawyer and senior counsel at the Department of Justice. So, there’s the question of liability, i.e., whether the software developer or manufacturer are held to a standard of strict liability, and what kind of ethical considerations are involved.
Let's personalize your content