Airplane manufacturer Bombardier has disclosed a security breach, data leaked online
Security Affairs
FEBRUARY 24, 2021
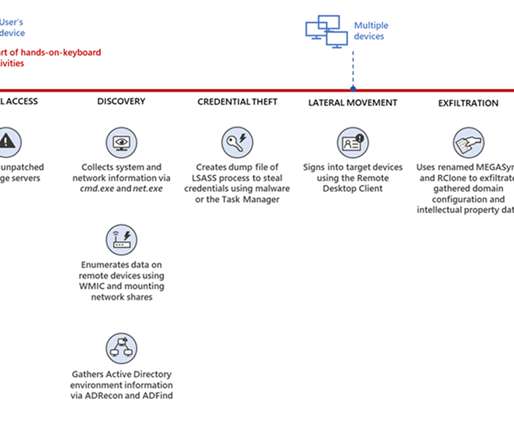
Hackers exploited vulnerabilities in Accellion FTA file-sharing legacy servers to steal data from the airplane maker Bombardier and leak data on the site operated by the Clop ransomware gang. Security experts from FireEye linked the cyber attacks to the cybercrime group UNC2546, aka FIN11.




















Let's personalize your content