Korean cybersecurity agency released a free decryptor for Hive ransomware
Security Affairs
JUNE 30, 2022
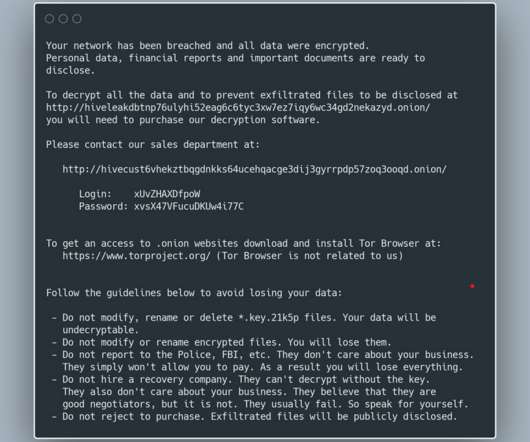
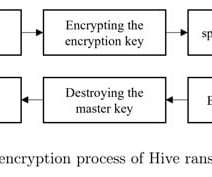
According to a report published by blockchain analytics company Chainalysis, the Hive ransomware is one of the top 10 ransomware strains by revenue in 2021. The malware is extracted from a specific offset of the master key 1MiB and 1KiB of data for each file to be encrypted and uses as a keystream.












Let's personalize your content