Experts warn of an emerging Python-based credential harvester named Legion
Security Affairs
APRIL 17, 2023
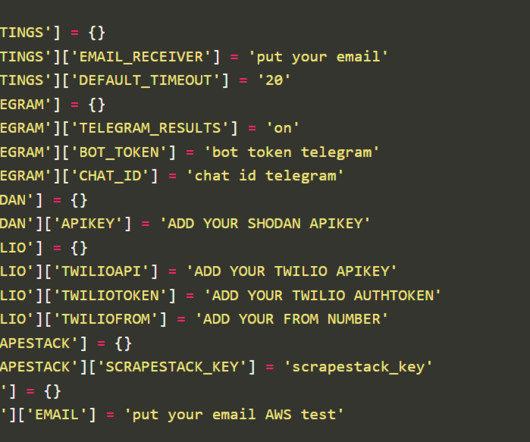
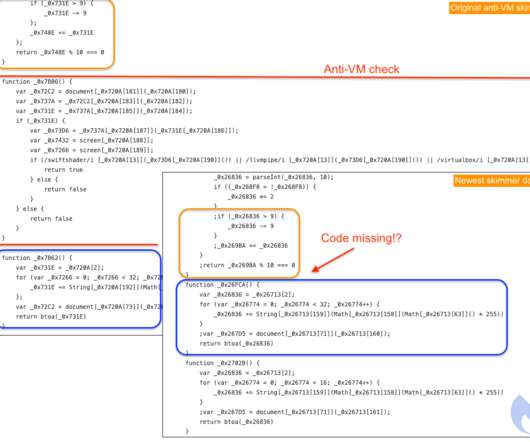
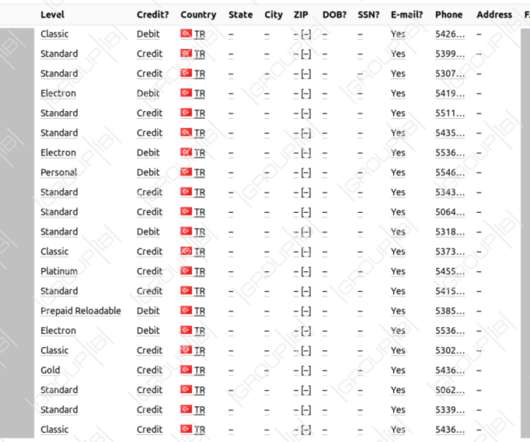
Legion exploits web servers running Content Management Systems (CMS), PHP, or PHP-based frameworks such as Laravel. “From these targeted servers, the tool uses a number of RegEx patterns to extract credentials for various web services. ” reads the analysis published by Cado Labs.

















Let's personalize your content