Operation Blacksmith: Lazarus exploits Log4j flaws to deploy DLang malware
Security Affairs
DECEMBER 12, 2023
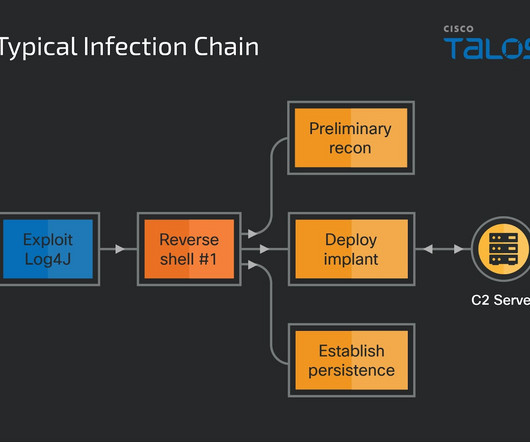
Two of these malware strains are remote access trojans (RATs), respectively tracked as NineRAT and “DLRAT” The former relies on Telegram bots and channels for C2 communications. In March, the threat actors hit a South American agricultural organization.





















Let's personalize your content