Raspberry Robin malware used in attacks against Telecom and Governments
Security Affairs
DECEMBER 24, 2022
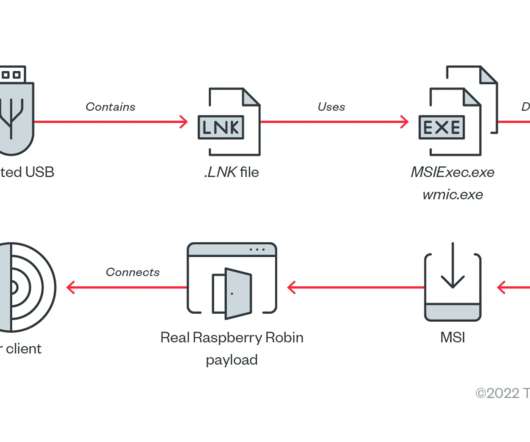
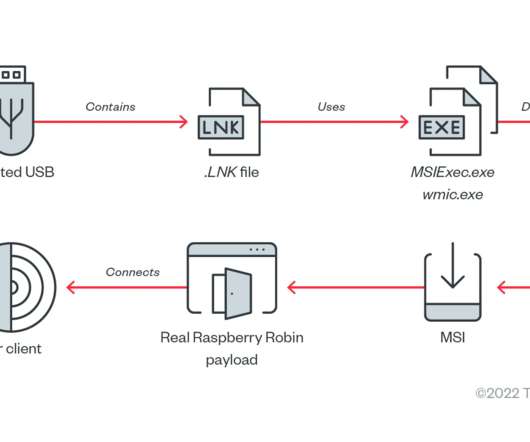
Researchers from Trend Micro have uncovered a Raspberry Robin worm campaign targeting telecommunications and government office systems across Latin America, Australia, and Europe. ” reads the report published by Trend Micro. ” reads the report published by Trend Micro. exe to execute a malicious command.














Let's personalize your content