Lazarus malware delivered to South Korean users via supply chain attacks
Security Affairs
NOVEMBER 16, 2020
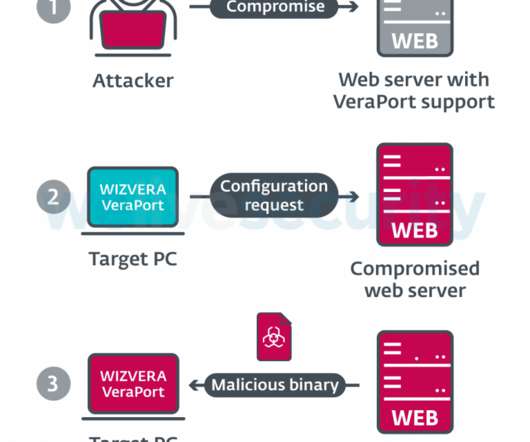
North Korea-linked Lazarus APT group is behind new campaigns against South Korean supply chains that leverage stolen security certificates. . Security experts from ESET reported that North-Korea-linked Lazarus APT (aka HIDDEN COBRA ) is behind cyber campaigns targeting South Korean supply chains. ” Pierluigi Paganini.
















Let's personalize your content