Operation Blacksmith: Lazarus exploits Log4j flaws to deploy DLang malware
Security Affairs
DECEMBER 12, 2023
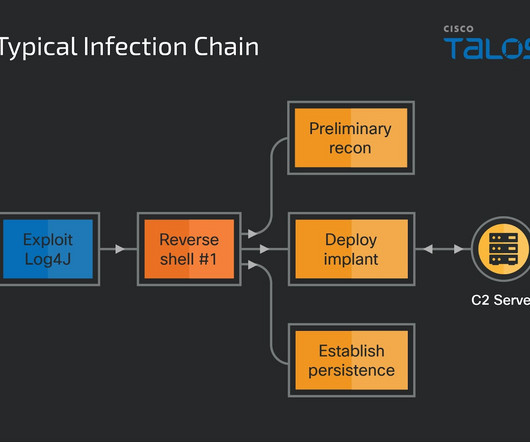
Talos believes that NineRAT was built around May 2022, but was first spotted on March 2023 as part of Operation Blacksmith. The experts observed the use of NineRAT at around September 2023 against a European manufacturing entity. In March, the threat actors hit a South American agricultural organization.













Let's personalize your content