Strategize your next move to become a utilities leader, delivering value at scale and pace
CGI
FEBRUARY 2, 2020
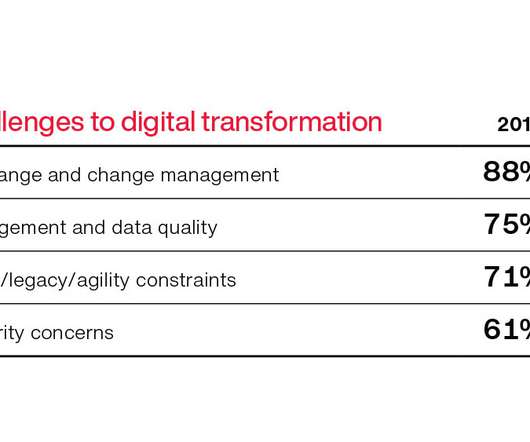
Strategize your next move to become a utilities leader, delivering value at scale and pace. Mon, 02/03/2020 - 01:59. Additionally, utilities leaders say their IT investments have increased, and they have moved beyond progressing with discrete digital projects, such as mobile applications.























Let's personalize your content