Russia-linked APT28 targets government Polish institutions
Security Affairs
MAY 10, 2024
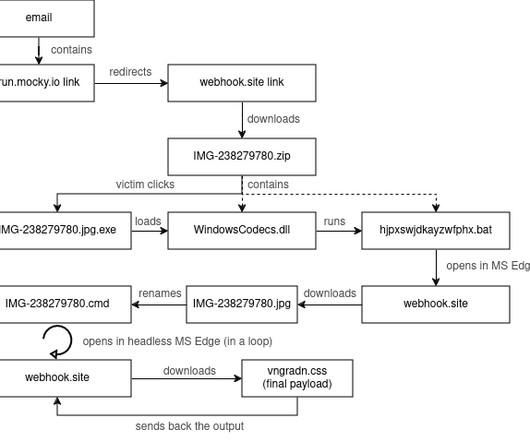
jpg.exe , which pretends to be a photo and is used to trick the recipient into clicking on it, script.bat (hidden file), fake library WindowsCodecs.dll (hidden file). The group was involved also in the string of attacks that targeted 2016 Presidential election. The attack chain includes the download of a ZIP archive file from webhook[.]site,














Let's personalize your content