Exclusive: Researchers dumped Gigabytes of data from Agent Tesla C2Cs
Security Affairs
OCTOBER 6, 2021
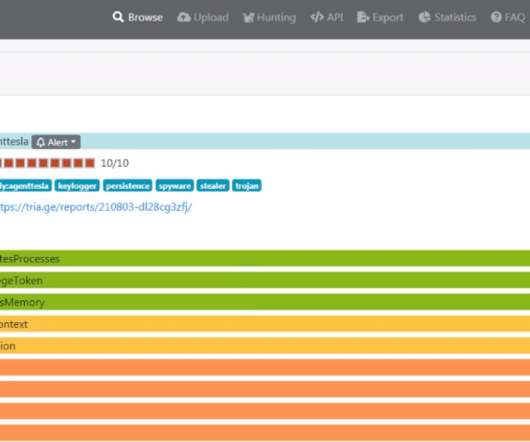
Agent Tesla , first discovered in late 2014, is an extremely popular “malware-as-a-service” Remote Access Trojan (RAT) tool used by threat actors to steal information such as credentials, keystrokes, clipboard data and other information from its operators’ targets.










Let's personalize your content