Who’s Behind the Botnet-Based Service BHProxies?
Krebs on Security
FEBRUARY 24, 2023
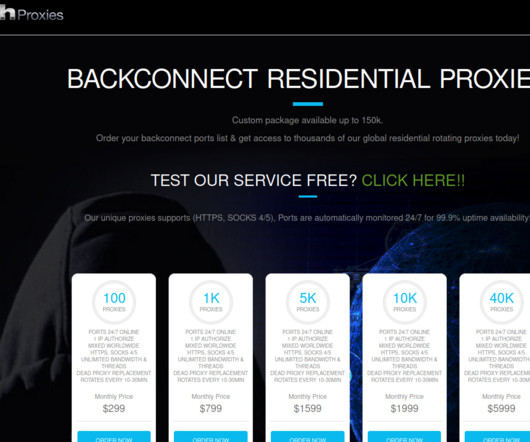
A security firm has discovered that a six-year-old crafty botnet known as Mylobot appears to be powering a residential proxy service called BHProxies , which offers paying customers the ability to route their web traffic anonymously through compromised computers. The BHProxies website. The website BHProxies[.]com

















Let's personalize your content