Ask Fitis, the Bear: Real Crooks Sign Their Malware
Krebs on Security
JUNE 1, 2023
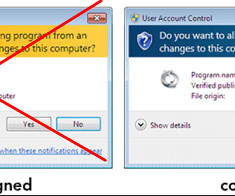
Megatraffer explained that malware purveyors need a certificate because many antivirus products will be far more interested in unsigned software, and because signed files downloaded from the Internet don’t tend to get blocked by security features built into modern web browsers. “Why do I need a certificate? Image: Archive.org.














Let's personalize your content