Naikon APT group uses new Nebulae backdoor in attacks aimed at military orgs
Security Affairs
APRIL 28, 2021
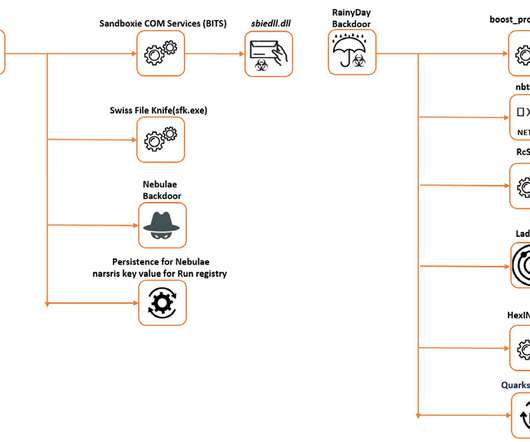
China-linked APT Naikon employed a new backdoor in multiple cyber-espionage operations targeting military organizations from Southeast Asia in the last 2 years. The Naikon APT group mainly focuses on high-profile orgs, including government entities and military orgs. Follow me on Twitter: @securityaffairs and Facebook.















Let's personalize your content