TMChecker Tool Lowers Barrier for Malicious Hacking
Data Breach Today
MARCH 18, 2024
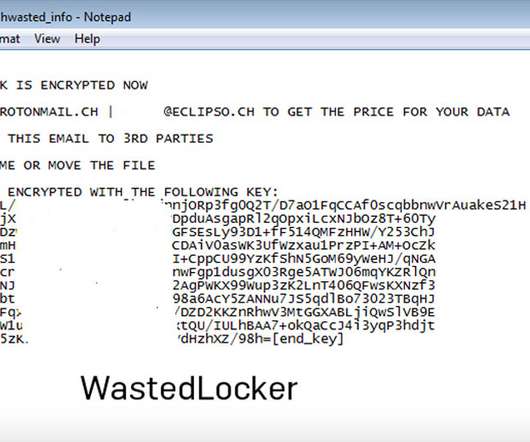
Tool Is Available for $200 a Month on Hacking Forums A new tool set on the dark web is gaining traction as an attack weapon to target remote access services and popular e-commerce platforms. TMChecker helps threat actors seeking to compromise corporate networks and gain unauthorized access to sensitive data.
















































Let's personalize your content