Security Affairs newsletter Round 334
Security Affairs
OCTOBER 3, 2021
Follow me on Twitter: @securityaffairs and Facebook. Pierluigi Paganini. SecurityAffairs – hacking, newsletter).

 tag payment-card-2
tag payment-card-2 
Security Affairs
OCTOBER 3, 2021
Follow me on Twitter: @securityaffairs and Facebook. Pierluigi Paganini. SecurityAffairs – hacking, newsletter).
Security Affairs
APRIL 24, 2020
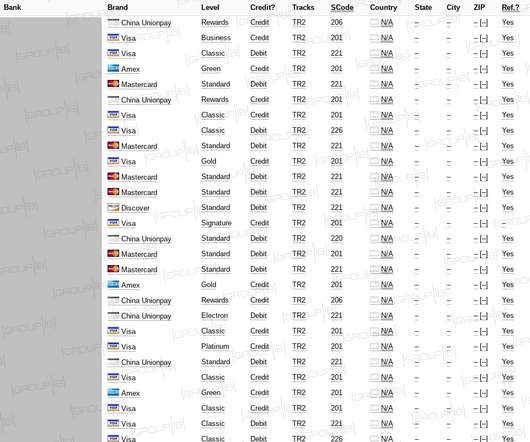
Group-IB experts discovere a dump containing details for nearly 400,000 payment card records uploaded to a popular darknet cardshop on April 9. The database was comprised almost entirely of the payment records related to banks and financial organizations in South Korea and the US. The provenance of this data remains unknown.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Data Matters
AUGUST 19, 2020
2 Because First American’s violations included the exposure of millions of documents containing nonpublic information (NPI), the total penalty potentially could be substantial. The NYDFS alleges in April 2018, FAST contained 753 million documents, 65 million of which had been tagged by First American’s employees as containing NPI.

Security Affairs
NOVEMBER 19, 2020
The experts observed an increased overlap of domain infrastructure used by multiple threat actors spreading software skimmers focused on the theft of payment card data from e-stores. . Hacker groups under the Magecart umbrella continue to target e-stores to steal payment card data with software skimmers.

IT Governance
MARCH 5, 2024
Data apparently includes users’ full names, phone numbers, addresses, email addresses and partial payment card information. million data records belonging to EasyPark have been listed for sale on a hacking forum. Data breached: 21,100,000 records.
Troy Hunt
AUGUST 21, 2023
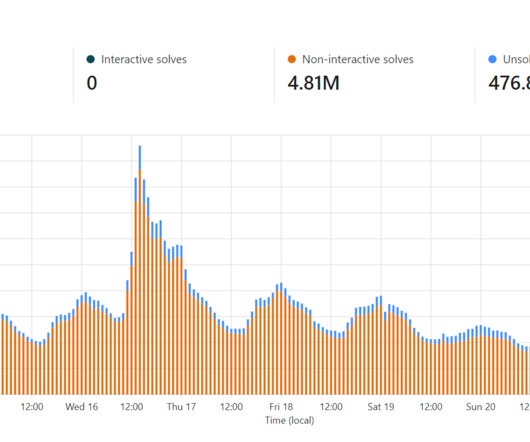
Problem is, that was a very rudimentary IP-based rate limit and it could be circumvented by someone with enough IPs, so fast forward a bit further and I put auth on the API which required a nominal payment to access it. So, 2 APIs with 2 different purposes. That remaining 9% is either humans with a false positive or.

Adapture
MAY 18, 2021
The success of a phishing attack highly depends on its ability to dupe the recipient into: 1) believing the email is legit and then 2) performing the call-to-action. It’s also a way of circumventing the ‘insecure’ labels popular browsers now tag HTTP sites with. Here’s an overview of what this type of attack entails.
Let's personalize your content