New skimmer attack uses WebSockets to evade detection
Security Affairs
NOVEMBER 15, 2020
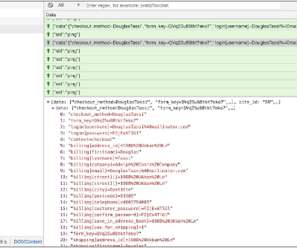
Once executed, a malicious JavaScript file is requested from the a C2 server (at https[:]//tags-manager[.]com/gtags/script2 The distinctive aspect of this attack is the use of WebSockets, instead of HTML tags or XHR requests, to extract the information from the compromised site that makes this technique more stealth.























Let's personalize your content