Identity Thieves Bypassed Experian Security to View Credit Reports
Krebs on Security
JANUARY 9, 2023
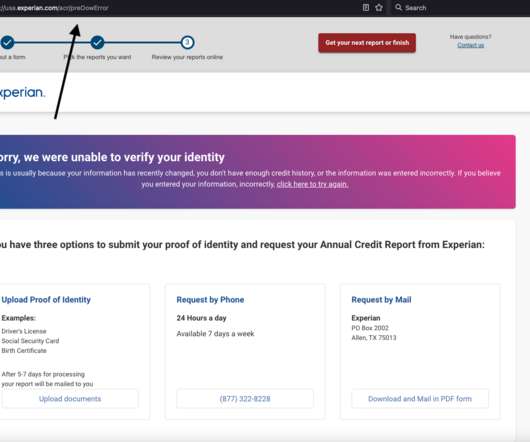
Identity thieves have been exploiting a glaring security weakness in the website of Experian , one of the big three consumer credit reporting bureaus. All that was needed was the person’s name, address, birthday and Social Security number. It wouldn’t even show me the four multiple-guess questions.













Let's personalize your content