Panasonic Warns That IoT Malware Attack Cycles Are Accelerating
WIRED Threat Level
AUGUST 9, 2023
The legacy electronics manufacturer is creating IoT honeypots with its products to catch real-world threats and patch vulnerabilities in-house.

WIRED Threat Level
AUGUST 9, 2023
The legacy electronics manufacturer is creating IoT honeypots with its products to catch real-world threats and patch vulnerabilities in-house.

Security Affairs
JUNE 22, 2019
The malicious code attempt to determine if it is running in a honeypot , then it downloads the payload and changes its permission settings to allow its execution. In order to determine what miner to deliver, the bot collects system information, such as manufacturer, hardware details, and processor architecture. The script for a.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Security Affairs
APRIL 28, 2020
The purpose of the script is to optimize the mining module by querying the information about the CPU through the reading of the “ /proc/cpu ” and when the manufacturer is retrieved the script provides to add some specific registry values depending by the vendor through the Model-Specific Register utility “ wrmsr ”. Sample information.
Security Affairs
MAY 12, 2021
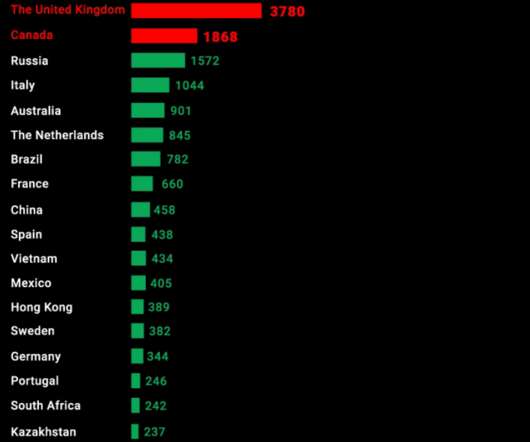
Our research shows that large and small manufacturers are identifiable, with Aastra-Mitel topping the list. Aastra-Mitel tops the manufacturer list, the United States leads the list among countries, and London tops the chart among cities. Devices made by the US manufacturer Polycom, a subsidiary of Plantronics Inc., What we did.

Security Affairs
SEPTEMBER 30, 2019
But let’s go back to the beginning of the story when my very good friend @0xrb found in his honeypot this new “ Mirai like ” Linux malware, which has important differences with the Mirai implementation. After 2 years of waiting, MalwareMustDie returns with an excellent page of malware analysis of a new IoT malware: Linux/AirDropBot.

eSecurity Planet
MARCH 23, 2022
Manufactured BackDoor Vulnerabilities. After persistence has been obtained, attackers may push the envelope to see which attacks will raise alerts. Once determining the threshold of the IT defenders, the APT attackers will proceed with their agenda using techniques designed to fall below the IT defender radar. APT Examples.

eSecurity Planet
MARCH 22, 2023
Operating technology (OT), also known as the industrial internet of things (IIoT), uses smart pumps, conveyor belts, motors, and manufacturing equipment — and the operations teams that install the devices may not always inform the network security team about them. Organizations need to verify the types of assets that will be detected.
Let's personalize your content