China-linked APT10 leverages ZeroLogon exploits in recent attacks
Security Affairs
NOVEMBER 18, 2020
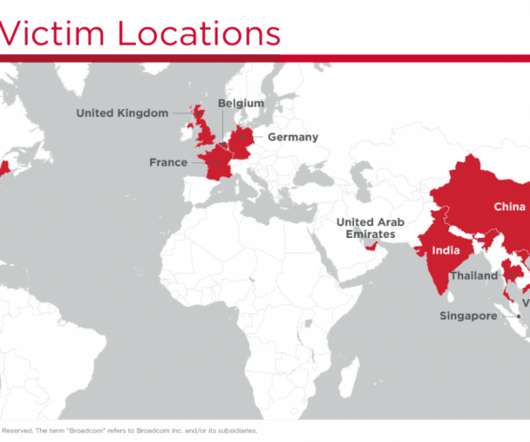
Researchers uncovered a large-scale campaign conducted by China-linked APT10 targeting businesses using the recently-disclosed ZeroLogon vulnerability. . The APT10 is well-resourced cyberespionage group that employed multiple tools and sophisticated techniques in its attacks. ” reads the report published by Symantec.











Let's personalize your content