China-linked Budworm APT returns to target a US entity
Security Affairs
OCTOBER 13, 2022
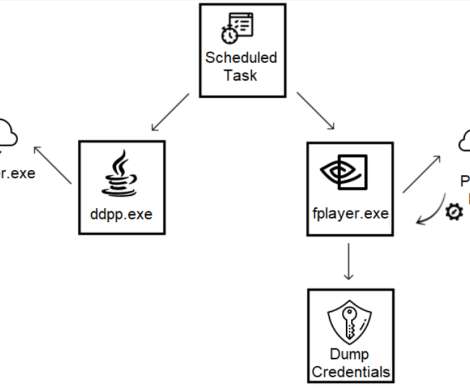
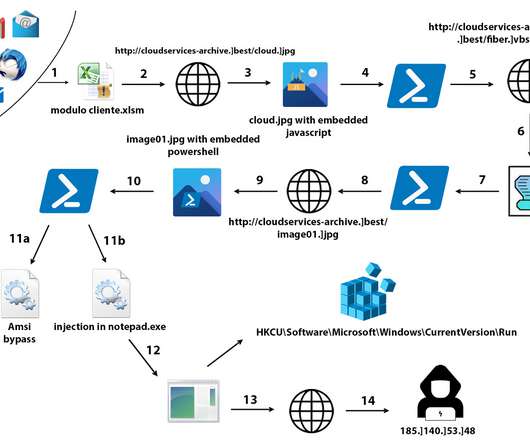
The cyber espionage group leverage both readily available tools and custom malware in their operations, many tools are available for years, but in recent attacks, their code was updated. The attackers continue to use the HyperBro backdoor which is often loaded using the dynamic-link library (DLL) side-loading technique.


















Let's personalize your content