Evilnum APT used Python-based RAT PyVil in recent attacks
Security Affairs
SEPTEMBER 3, 2020
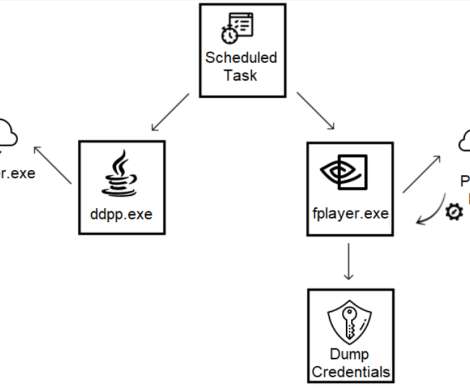
Over the years, the group added new tools to its arsenal, including custom and homemade malware along with software purchased from the Golden Chickens malware-as-a-service (MaaS) provider. The second layer of Python code decodes and loads to memory the main RAT and the imported libraries. The PyVil RAT stores the malware settings (i.e.













Let's personalize your content