Researchers disclose critical sandbox escape bug in vm2 sandbox library
Security Affairs
APRIL 9, 2023
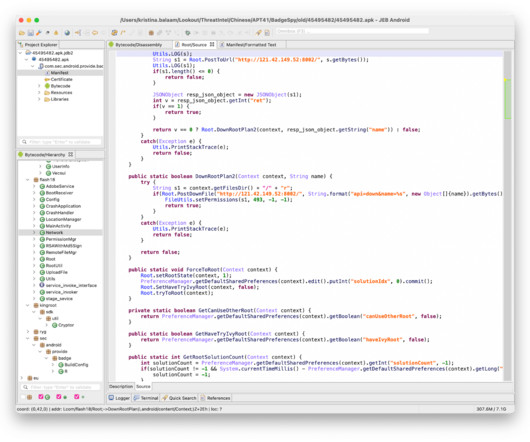
The development team behind the vm2 JavaScript sandbox library addressed a critical Remote Code Execution vulnerability. servers, it has approximately four million weekly downloads and its library is part of 722 packages. servers, it has approximately four million weekly downloads and its library is part of 722 packages.


































Let's personalize your content