The Scammers’ Playbook: How Cybercriminals Get Ahold of Your Data
eSecurity Planet
SEPTEMBER 14, 2022
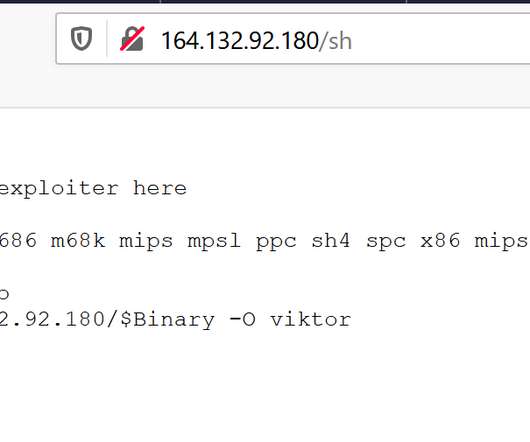
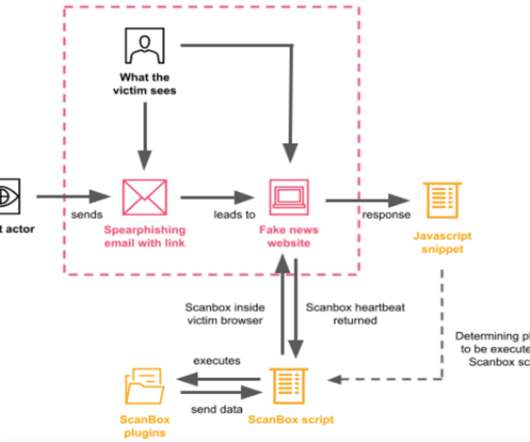
As a matter of fact, the most-reported crime in the 2021 Internet Crime Report report was phishing , a social engineering scam wherein the victim receives a deceptive message from someone in an attempt to get the victim to reveal personal information or account credentials or to trick them into downloading malware. Technological tactics.

















Let's personalize your content