US Energy Utilities Targeted by FlowCloud Malware
Data Breach Today
JUNE 9, 2020
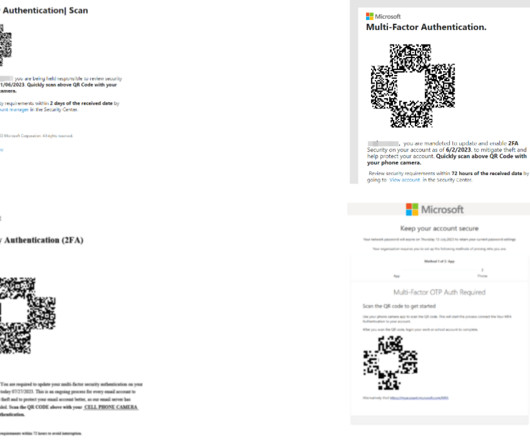
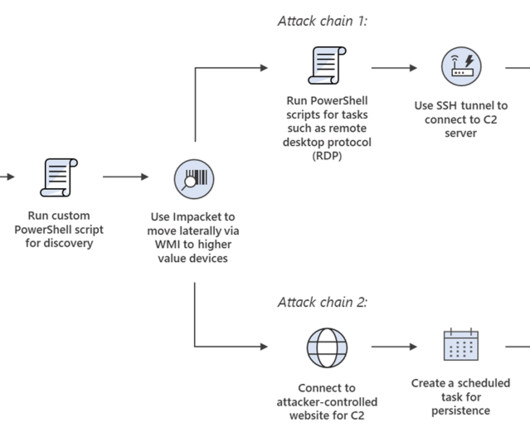
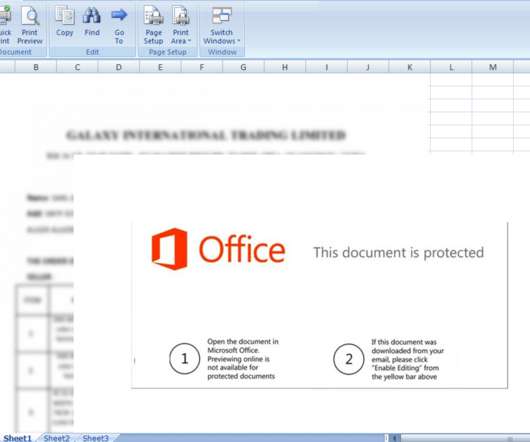
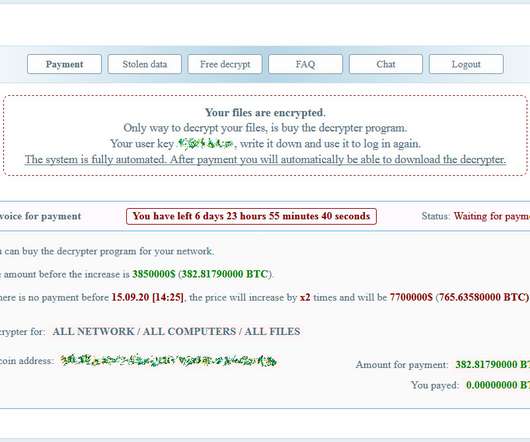
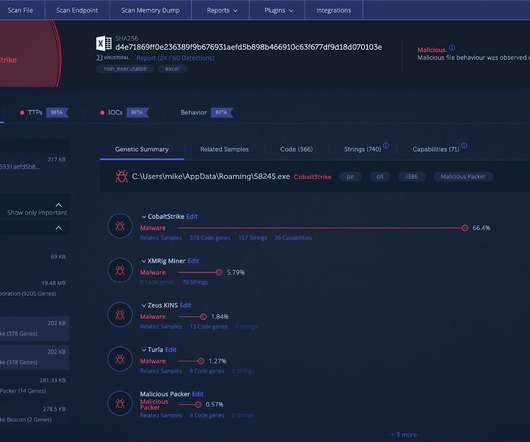
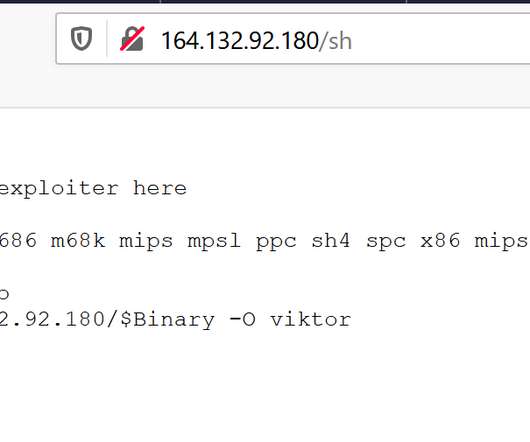
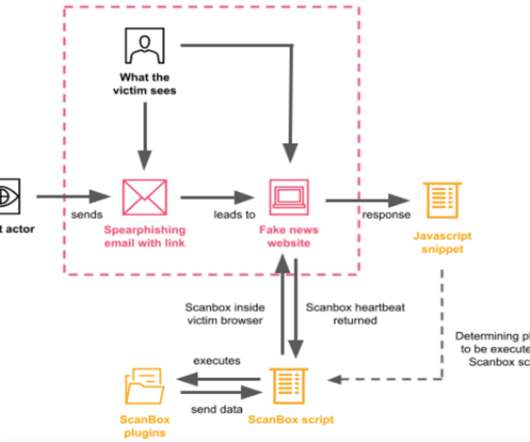
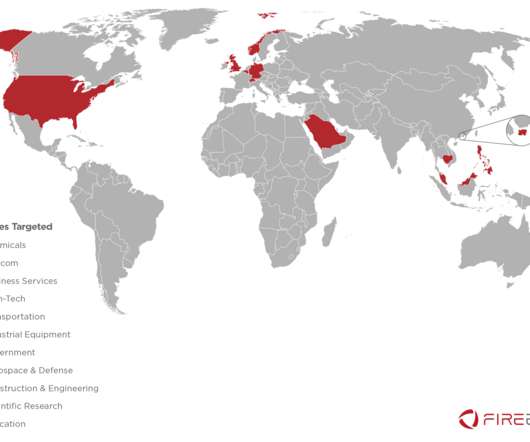
energy providers have been targeted by a spear-phishing campaign attempting to spread a recently discovered Trojan called FlowCloud, according to Proofpoint research. Proofpoint Analysts Find Connections Between New Trojan and Other Attacks Several U.S.
































Let's personalize your content