Can visibility be the key to better privacy?
Thales Cloud Protection & Licensing
DECEMBER 8, 2020
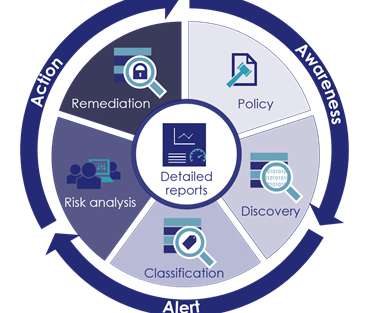
A research report issued by International Association of Privacy Professionals titled “Privacy in the wake of COVID-19” shows that 60 percent of those who adopted new technologies for working from home either skipped or expedited security/privacy reviews, creating a completely new set of risks for companies.













Let's personalize your content