Protecting Sensitive Data with Luna Key Broker for Microsoft Double Key Encryption
Thales Cloud Protection & Licensing
APRIL 1, 2021
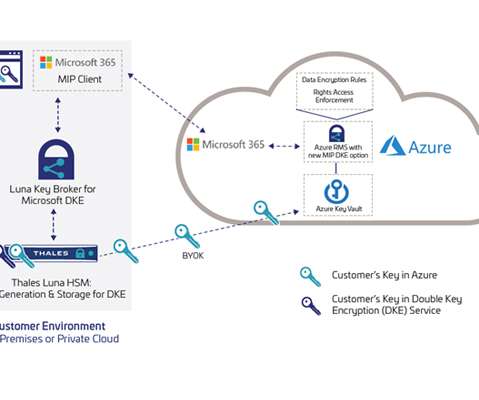
Protecting Sensitive Data with Luna Key Broker for Microsoft Double Key Encryption. Thales has integrated its Luna HSMs with DKE for Microsoft 365, which work together to enable organizations to protect their most sensitive data while maintaining full control of their encryption keys. Thu, 04/01/2021 - 14:04.
























Let's personalize your content