REvil's Ransomware Success Formula: Constant Innovation
Data Breach Today
JULY 2, 2021
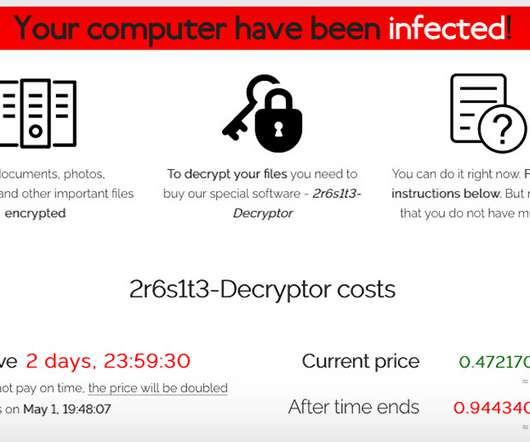
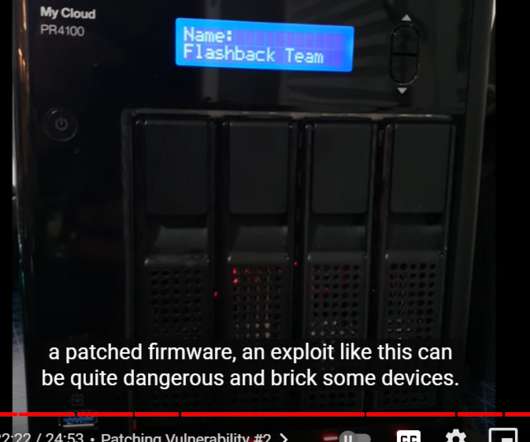
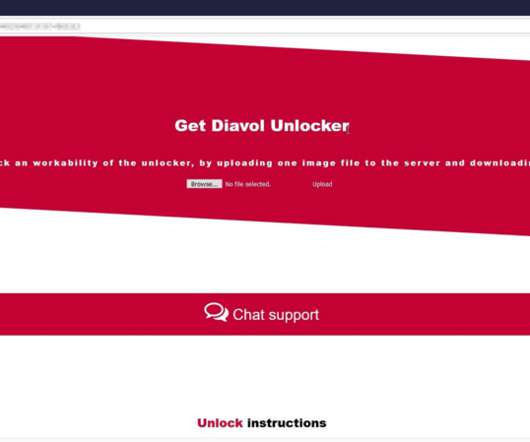
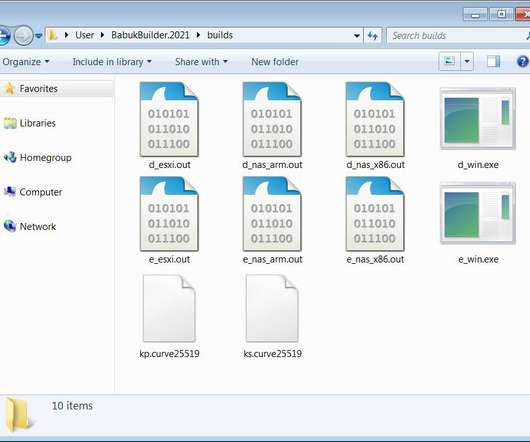
Affiliate-Driven Approach and Regular Malware Refinements Are Key, Experts Say REvil, aka Sodinokibi, is one of today's most notorious - and profitable - ransomware operations, driven by highly skilled affiliates who share profits with the operators. And the operators are constantly improving the malware, including porting it to Linux to target network-attached storage and hypervisors.


































Let's personalize your content