Microsoft Office: Attackers Injecting Code via Zero-Day Bug
Data Breach Today
MAY 30, 2022
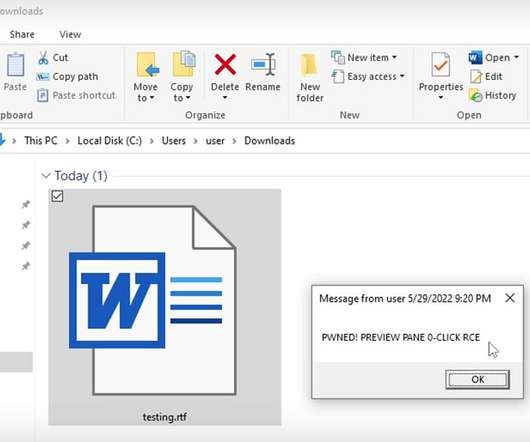
Malicious Code Execution Traced to Weaponized Office Documents Dating From April Attention to anyone who manages a Microsoft Windows environment: Security researchers are tracking a zero-day vulnerability in Microsoft Office that's being actively exploited by attackers to run malicious code on a vulnerable system.





























Let's personalize your content