Mobile Banking Users Targeted in SMS Phishing Campaign
Data Breach Today
FEBRUARY 18, 2020
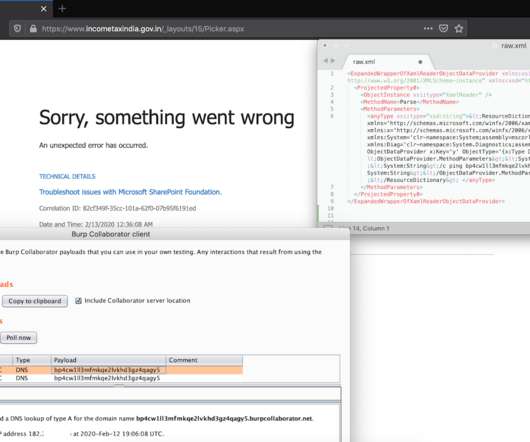
Researchers Say Attackers Targeted American and Canadian Banking Customers Cybercriminals targeted mobile banking users by sending malicious SMS messages to their smartphones as part of a phishing campaign to steal account holders' information, including usernames and passwords, according to the cybersecurity firm Lookout.







































Let's personalize your content