More Zero-Day Exploits For Sale: Report
Data Breach Today
APRIL 8, 2020
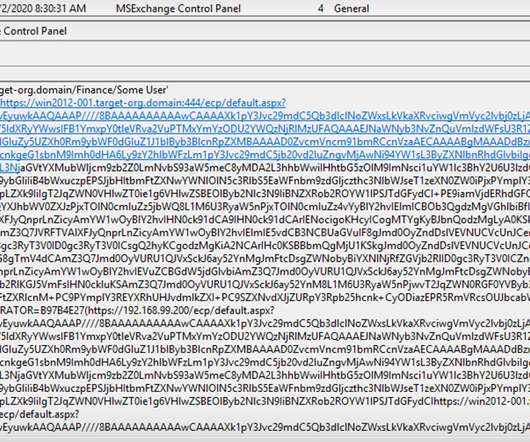
APT Groups Are Buying Exploits Rather Than Developing Them, FireEye Says Zero-day exploits are increasingly a commodity that advanced persistent threat groups can purchase and use to wage attacks, according to a report from security firm FireEye. The report says the number of attacks leveraging such exploits grew last year.







































Let's personalize your content