Chilean-based retail giant Cencosud hit by Egregor Ransomware
Security Affairs
NOVEMBER 15, 2020
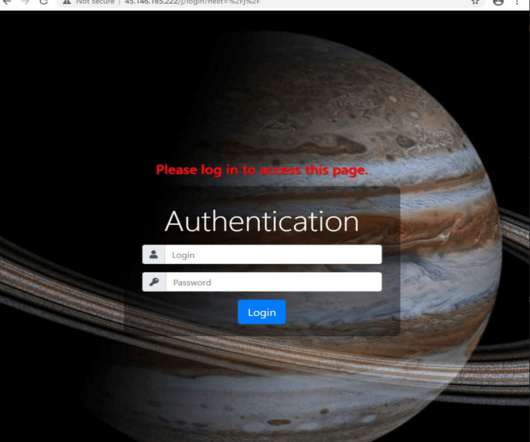
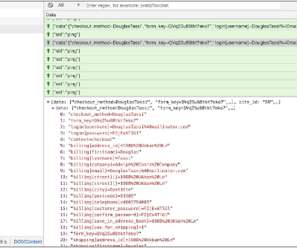
Chilean-based retail giant Cencosud has suffered a ransomware attack that impacted operations at its stores, Egregor ransomware appears to be involved. A ransomware attack, allegedly launched by the Egregor ransomware gang, hit the Chilean-based retail giant Cencosud, the incident impacted operations at its stores. Cencosud the largest retail company in Chile and the third largest listed retail company in Latin America, competing with the Brazilian Companhia Brasileira de Distribuição and the Me




















Let's personalize your content